The Russian hacker troop is called “Evil Corp” and is said to be behind the hacker attack on Garmin. With their ransomware “WastedLocker”, the hackers have brought one of the most renowned navigation companies in the world, Garmin, to its knees for a few days. On July 23rd, Evil Corp boarded Garmin’s systems with WastedLocker, and only on June 27th, some of the Garmin services were available again. How long the hackers have been in the systems is not yet known, but the existence of WastedLocker has been known for a month: On June 23rd, NCC Group security researchers announced that Evil Corp has developed a new ransomware. This news immediately caused a stir in the banking scene, because the Evil Group is also behind the banking Trojan Dridex, with which the company has (successfully) extorted millions. Behind the Evil Group is said to be the Russian Maksim Viktorovich Yakubets, for whom the FBI put out a bounty of 5 million dollars at the end of 2019.

Screenshot
The fact that Garmin is becoming a ransomware victim is surprising, since one would assume that a technology company of this size (about three billion dollars turnover per year) and with this decades of experience (founded in 1989, the company headquarters is in Schaffhausen, Switzerland, the technical headquarters in Olathe Kansas/USA) should have done its IT security homework. The fact is that at Garmin, a person has made a mistake – either someone has clicked where he/she should not have clicked or the IT administrator has not protected the systems well enough, has not installed updates or left security holes open. I also write about this in detail in my book.
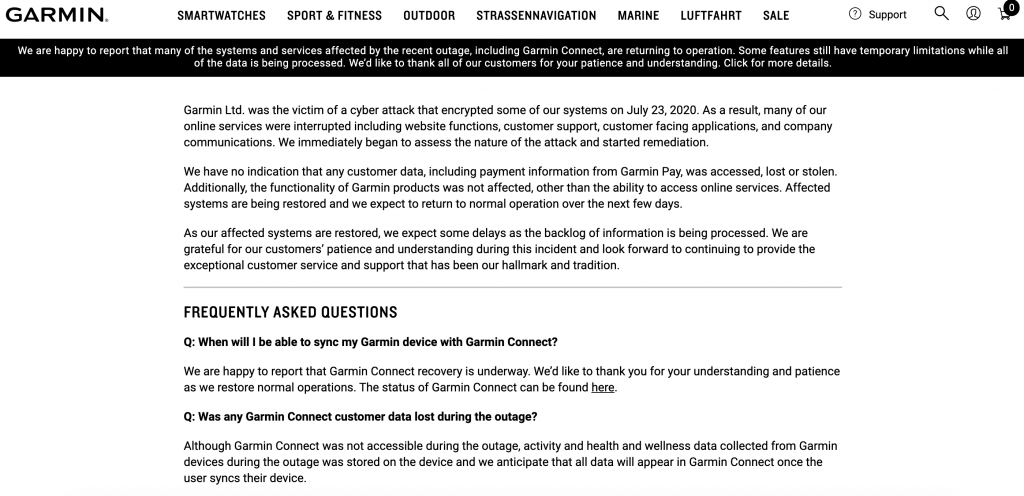
With messages such as “Oops, your files have been encrypted”, ransomware reveals itself when it’s too late – the files are encrypted and no longer accessible to the company. Only after paying a ransom, the hackers release the data. The amount of the ransom is often based on the amount of turnover, in the case of Garmin the hackers are said to have demanded 10 million dollars. Whether Garmin actually paid this sum (in Bitcoin) and how much of the data could be recovered with the help of IT specialists, Garmin has not yet disclosed. By the way, Garmin has not admitted to having been a victim of an attack for a long time. The official statement read: “Garmin is currently experiencing a system failure that affects Garmin services, including Garmin Connect. As a result of the outage, some features and services on these platforms are not available to customers. In addition, our product support is affected by the outage, so we are currently unable to receive calls, emails or online chats. We are working continuously to restore our systems as quickly as possible and apologize for the inconvenience. Further updates will be provided as soon as they are available.”
Screenshot
It’s also possible that Garmin was negotiating with the cybercriminals. This was also reported by representatives of the University of California in San Francisco (UCSF) in early June, who have been searching for a vaccine against the coronavirus SARS-CoV-2 practically since the outbreak of the COVID-19 pandemic. Hackers had lamed the laboratory’s system on 1 June by ransomware and demanded a ransom. Knowing that UCSF has an annual turnover of $7.5 billion and receives more than $300 million in donations annually, the hackers demanded a $3 million ransom. In the days that followed, UCSF representatives negotiated with the hackers via a chat function in the blackmail software and were able to agree on a ransom of $1,140,895. In the form of 116.4 Bitcoins they transferred it – contrary to the opinion of the police – to the cybercriminals’ wallet, received the decryption software the next day and the research data was saved.
Back to the Garmin hack: It is particularly explosive in that Garmin stores physical user data and health data in Darkweb is now worth more than credit card data. Such information can be used for marketing purposes, for example to advertise health and nutrition products. In general, such addresses are interesting for spam mails, but also for insurance companies – it cannot be excluded that criminals also offer insurance companies stolen health data. I hope and assume that, if the worst comes to the worst, European insurance companies will not take action or will be weakened. It is also worth mentioning that such data can of course be manipulated – a healthy person becomes a sick one – or vice versa.
Whether the Garmin hack is successful or not, the question now arises as to whether such companies can still be trusted, whether health data at Apple, Polar and what these companies are called are safe. Basically yes, but the data is as secure as the IT administrators keep their systems secure. The fact is that ransomware attacks will become more frequent – not only large companies such as Garmin will be attacked, but also small and medium-sized companies. And also private individuals. It happens more often than you think, because many victims do not go to the police and pay. And companies avoid talking about it because they also fear damage to their image.



Leave A Comment